Do you know what is Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks? Or how to DDoS someone in 2022? How to DDoS on Xbox console.
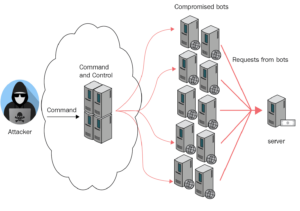
Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks are malicious efforts to overload a targeted server, service, or network with a flood of Internet traffic in order to interrupt its regular operations.
DoS attacks work by transmitting malicious traffic from a single machine, usually a computer, to cause a disturbance. Do you know how to DDoS someone in 2021? They can be quite simple. For example, a simple ping flood attack can be carried out by sending more ICMP (ping) queries to a targeted server than it can properly process and respond to.
Los dos carnales assaults, on the other hand, deliver harmful traffic to a target from many machines. These machines are frequently part of a botnet, which is a network of infected computers or other devices that can be controlled remotely by a single attacker. In other cases, a group of attackers collaborate to initiate DDoS assaults by sending bandwidth from their own machines. How to DDoS someone in Xbox? How to DDoS on Xbox console.
Because of two factors, DDoS discord assaults are increasingly common and harmful on today’s Internet. First, contemporary security tools have improved to the point where they can now thwart some common DoS equis assaults. Second, DDoS discord attack tools have gotten more affordable and simple to use.
What is the difference between DoS and DDoS attack tools?
There are several tools that may be customised or are specifically built to launch DoS equis / DDoS discord assaults. The former group frequently includes “”stressors”” – tools designed to assist security researchers and network engineers in conducting stress testing on their own networks, but which may also be used to launch actual assaults. Some are focused on a single layer of the OSI model, while others are built to handle numerous attack routes.
Low and sluggish attack tools are examples of attack tools. These attack tools, as the name indicates, function slowly and consume a little amount of data. These tools are designed to transfer little quantities of data over numerous connections in order to keep ports on a targeted server open for as long as possible.
They continue to eat up the server’s resources until it can no longer support new connections. Low and slow assaults, on the other hand, are often employed by a single computer and may be effective even when not employing a distributed system like a botnet. How to DDoS on Xbox console.
How to DDoS someone: L7 attack tools (application layer)
These tools are aimed towards layer 7 of the OSI model, which is where HTTP requests and other Internet-based requests happen. A malicious actor can launch attack traffic that is difficult to differentiate from legitimate visitor requests by using an HTTP flood attack to overwhelm a target with HTTP GET and POST requests.
Tools for attacking the protocol and transport layers (L3/L4)
These tools use protocols like UDP to deliver massive amounts of traffic to a targeted server, such as during a UDP flood. While ineffectual on their own, these assaults are most commonly encountered in the form of DDoS discord attacks, in which the effect is amplified by the addition of more assaulting computers.
What are some of the most widely utilized DoS/DDoS attack tools?
The Low Orbit Ion Cannon (LOIC) is a widely used instrument (LOIC). The LOIC is a stress-testing programme that is free and open-source. It has a user-friendly WYSIWYG interface that enables both TCP and UDP protocol layer assaults. Because of the original tool’s popularity, variants have been developed that allow assaults to be launched from a web browser.
Ion Cannon with Extremely High Orbit (HOIC). This attack tool was designed to take the role of the LOIC by enhancing its capabilities and providing modifications.
The HOIC may conduct targeted assaults that are tough to defend against by using the HTTP protocol. The programme is intended for a coordinated assault attempt involving at least 50 people. Slowloris is a type of slow loris. Slowloris is a programme that launches a low-level, slow-moving assault on a specific server. To have a harmful effect, it just needs a little number of resources.
R.U.D.Y. is an acronym for “reduce, reuse, and recycle” (R-U-Dead-Yet) R.U.D.Y. is a low-and-slow attack tool that uses a simple point-and-click interface to allow users to launch assaults quickly. The attack tries to gradually overwhelm the targeted server by sending numerous HTTP POST requests and keeping those connections open for as long as feasible.
How can I protect myself against DoS/DDoS attacks?
Because DoS equis and DDoS discord assaults may take many different forms, defending against them necessitates a wide range of strategies. how to ddos someone? Stopping DDoS equis assaults may be done in a number of ways. Rate limiting is the process of limiting the number of requests a server accepts in a certain time frame.
Firewalls for websites:
Tools that use a set of criteria to filter web traffic. Diffusion of an anycast network between a server and incoming traffic, providing additional computing resources to respond to requests.